Control types can be used in security polices to prevent and lower the risks in attacks. Control types can be a physical device or a piece of software. Other types of controls could also be a physical wall or fence protecting your building or biometric security doors. Overall, controls are a great way to protect the inner-diameter of your belongings from outside users. We will discuss many types of controls used within businesses throughout this article.
In a business, there are three types of controls that are used, Managerial, Operational, and Technical.
- Managerial Controls – These types of controls are provided by managers to reduce risk within companies. incorporation of regulatory frameworks such as HIPAA compliance, Part 11 compliance, and Privacy Shield are just some frameworks that strengthen the polices for IT in a company. Other types of managerial controls could be different types of security assessments or penetration and vulnerability tests.
- Operational Controls – Controls that provide day to day activities by the company users. Some examples of operational controls could be security training to end users. Operational controls provide most of the security in your company. IT administrators are taught that your security is just as good as your users are. Training employees on spam, fake websites, or file protection can save your company from internal attacks. Other types of controls used in operations are change management and business continuity/disaster recovery plans.
- Technical Controls – These controls provide security through the IT department on IT related equipment such as servers, networks, and end user computers. Some examples of technical controls could be prevention of specific websites through firewall black/white lists, lockdown of network ports on the firewall, and antivirus software on end user laptops and systems.
Physical Controls
There are many types of physical controls that can be used in any environment. Most physical controls are made to prevent unauthorized users into an area or room without their consent.
- Deterrent Controls – Cameras, sensors, and signs are a great way to prevent users from trying to access high level areas. The objective is to physical object react and be visible to the potential user when they are accessing an area.
- Detective Controls – These controls are often taken from the deterrent controls, camera recordings, log files, timestamps of sensors can help investigators look into any incident.
- Corrective Controls – Corrective controls is the process of correcting or fixing the issue. If a hard drive failed and you lost all the data on the drive, you would take corrective controls by restoring the data from a backup device.
- Compensating Controls – Controls that can assist with primary controls to complete an action. If a user is trying to sign into their laptop but is given a “password incorrect” error, the user can use biometric sign-in to login to the laptop instead.
- Preventative Controls – Preventing an attack either physical or virtual. Having a security guard at the front door or disabling accounts can help prevent unauthorized users from gaining access to internal systems.
Access Controls
With technology improving everyday, we have the ability to incorporate different types of hardware and software to provide means of access for our users. The most common type of access controls we use today are biometric and credentials. For any type of access control we have Identification, Authentication, and Authorization. Each type of access control allows the user to confirm their identity with the piece of hardware or software.

Step 1: Identification – Identify the user through use of an account. This could be associated with a card or any type of alphanumeric system which is given to the end user as their virtual ID. This is a way to match the identity of the user and provide access to the system.
Step 2: Authentication – Once the user has submitted their identification, they will then have to authenticate their identity. Authentication is usually provided by entering credentials such as a password or PIN.
Step 3: Authorization – A user that is created in a system has to be provided a form of authorization or be put in a group that has permissions of access to something. If John Doe is a member of the Financial Department group in active directory, he will ONLY be provided access to the files within the Financial Department.
Discretionary Access Controls
Every computer today has some form of access controls. We know that access controls are a way to prevent unwanted users from gaining access to a file, building, or room. In Windows, we can use access controls to prevent or have specific levels of access to a file or folder.
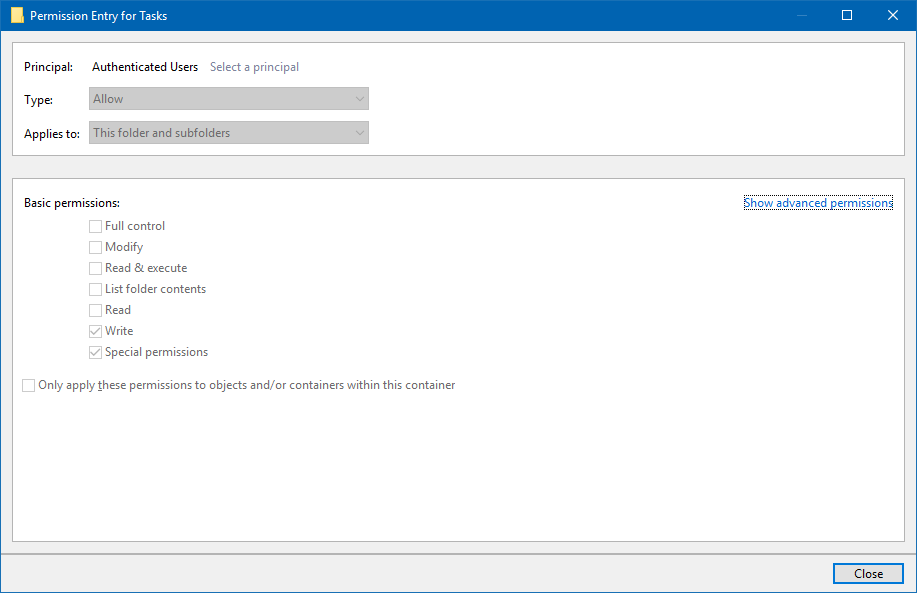
The properties of every file and folder in Windows offers different types of security depending on the specific user and what they need to access. The permissions used for each file or folder are given to either a specific user or group in the system.
- Full Control – Read, write, delete, replace, etc. The end user can do whatever they need to with the folder or file
- Modify – Change the file or folder as needed such as read and write to the file
- Read and Execute – Read the file or open the file as needed
- List Folder Contents – Expand the folder to view sub-folders and their contents
- Read – Open the file and read its contents
- Write – Write to the file by making changes to the file such as editing a document
- Special Permissions – Provide specific access to the content which is not given by the parent folder. We see this when a parent folder has “List Folder Contents” permissions but all the files within the parent folder have “Read” only permissions.
- Data Creator/Owner – The person that created the file or folder. Usually the one who can modify permissions for the file or folder for other users
As noted with “Special Permissions”, not all files and folders will have “Full Control” selected. Folders in Windows such as the ProgramData folder might be locked down to “Read” permissions for end users other than Administrators. While Administrators might have “Full Control” permissions.
Mandatory Access Controls
Mandatory access controls are different levels of security for determining the level of damage that could be inflicted on a file or system. We commonly see these controls within government agencies or high level departments that need to protect the integrity over their information.
4 Levels of Security
- Level 1 – Top Secret: Could cause exponential damage
- Level 2 – Secret: Could cause serious damage
- Level 3 – Confidential: Could cause normal amounts of damage
- Level 4 – Restricted: Undesirable effects or non-inflicting damage
Other Types of Controls
Role-Based Access Controls – Specific users have control of a single system. An example could be that only the network admins have access to the firewalls while help desk does not.
Rule-Based Access Controls – Creating a rule for when users can having access to any system during a specific time throughout the day.
Attribute Access Controls – Common controls found in active directory to allow users to a specific folder for viewing but only allow certain people within the department to have read/write attributes while others only have read attributes.
Group-Based Access Controls – Another common control found in active directory to allow specific groups (users/members of a business that categorized into groups) to have the same attributes or permissions to a file or folder.



