The CIA triad is the foundation of all security. It helps lay the polices used for any and all security infrastructures. CIA stands for Confidentiality, Integrity, and Availability.
Confidentiality: Prevention of disclosing information and data to unauthorized people.
Integrity: Knowing the information and data has not been altered
Availability: Making the information and data always available
Confidentiality
Keeping data confidential is important so no one else but the required users are able to see the information. Most of the time, confidentiality is locked to specific users by using permissions, also known as “Least Privilege” or a permission like security system. Other times, confidentiality can be kept by using encryption or hashing algorithms to scramble the data from being readable. There are two types of encryption we can use to scramble the data, symmetric and asymmetric.
- Symmetric – Uses one key, such as a private key or shared key
- Asymmetric – Uses two keys, such as a private key and a public key (Most Common)
Integrity
When data has been altered, this could cause an alarm for security professionals or could be considered a data breach. Integrity is just as important as confidentiality by making sure the data has not been modified, deleted, or updated when it is not supposed to be altered in any way. We can prevent integrity disasters by implementing many tools, but the best tool to use are hashing algorithms. Hashing is the use of converting the data into a numerical value. By hashing a file, a string of numbers are provided. Rehashing the same file will present the same numbers no matter what. Once there is a change within the file, hashing the file will output a different string of numbers.
Example
Lets say I have a file called “test.txt”. I can run the file through PowerShell to convert the file into a hash.
get-filehash C:\Users\Clien\Documents\test.txt
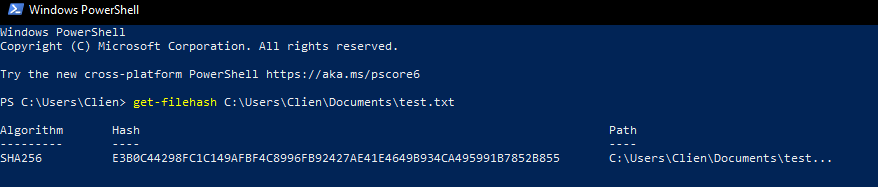
As you can see, we have the algorithm used which in this case is SHA256. We are then presented the hash for the file in both letters and numbers. Finally, we can see the file we used and where it is located. If I run the same command on the file once more, we can confirm the file has not been altered by confirming the hashes are the same values
Now lets say I made an edit/change to the file “test.txt” and then saved the file. When I run the “get-filehash c:\test.txt” command again, I will be present a different hash, meaning something has changed in the file which can help determine integrity.
While there are many types of hashing algorithms to use, the most common ones are SHA1, SHA2, SHA3, and MD5. SHA stands for Secure Hash Algorithm followed by the version number. MD5 stands for Message Digest followed by the version number. With each algorithm, the version gives us what the encryption bit is.
- SHA1 = 160-bit
- SHA2 = 256-bit
- SHA3 = 512-bit
- MD5 = 128-bit
When trying to decide on the encryption type to use, remember that the lower the bit number the faster the encryption will take. On the other hand, a lower bit number also means it will be less secure than a higher bit.
Availability
Availability is an expectation that every company hopes for when users need access to data on the network 24/7. IT professionals know that this is comical and not possible all the time. To curb availability disasters, we have many new technologies available to help us make our systems redundant. We can do this by using cloud or on-prem environments that are replicated and synced together.
Example
Lets say I have a file server that hosts all of my company’s data for my users to access over the network. By having the files stored on a server, I can setup network drives to make it easy for my users to access the files on the server. One day, the file server was appearing offline and my users were not able to access important files from the server. The network drives were showing they were offline and not connected to the file server. To prevent issues like this happening, I can setup a second file server that copies all the data between the two servers. So the next time one of the file servers go offline, the second file server can take over and provide access for my users without any downtime
Other types of availability could be cloud based such as Amazon buckets hosting files in the cloud rather than hosting them on-prem, VMware environments to replicate servers or easily manage servers and workstations or even RAID (Redundant Array of Independent Disks) setups which can replicate the just the data of a hard drive to another hard drive.
Defense in Depth Model
Defense in depth provides theoretical layers of protection within a company so that when a layer has been compromised, the next layer takes over. A defense in depth model can be a chart or visual representation of what happens when each layer is breached.
Example
- Layer 1 – Data is stored on a file server
- Layer 2 – Each of the files and folders on the server have permissions for accessing/modifying/deleting
- Layer 3 – The files and folders are encrypted and provided hashing algorithms for integrity
- Layer 4 – The server can only be logged in with administrators
- Layer 5 – The server can only be accessed when the administrator is in the office connected to the LAN network
- Layer 6 – The server is protected in a locked room
As we can see from the example, each layer provides different types of security for when one of the layers have been breached, the proceeding layer offers a higher protection level. Defense in depth models can have as many layers as needed. The more layers you have, the more secure and protected your systems will be.